By Lerpong Intaraworrapath | June 30th ,2023
VMware Cloud Foundation 5.0 is now available, as announced by the VMware Cloud Foundation team. This important platform update adds scalability, security, and other critical advancements to handle cloud scale infrastructure as a service (IaaS), easier on-premises cloud deployment, and enhanced cyberattack protection.
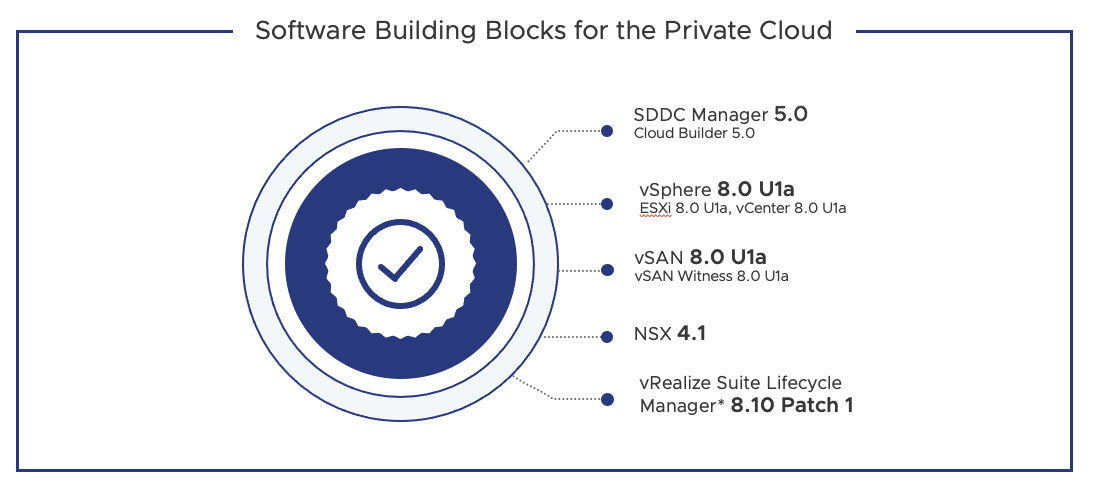
Software Building Blocks for the Private Cloud
- SDDC Manager 5.0 (Cloud Builder 5.0)
- vSphere 8.0 U1a (ESXi 8.0 U1a, vCenter 8.0 U1a)
- vSAN 8.0 U1a (vSAN Witness 8.0 U1a)
- NSX 4.1
- vRealize Suite Lifecycle Manager* 8.10 Patch 1
SDDC Manager Enhancements
VMware Cloud Foundation 5.0 includes a new capability called Isolated SSO Workload Domains, allow administrators the option to configure new workload domains using a separate Single Sign On (SSO) instance.
This scenario is useful for large enterprises that need workload isolation and for Managed Service Providers (MSPs) who can allocate workload domains to different tenants with their own SSO domains. Isolated SSO domains are each configured with their own NSX instance. The added benefit is that configuring workload domains as an isolated workload domain also allows the option to configure a separate identity provider (Active Directory or LDAP).
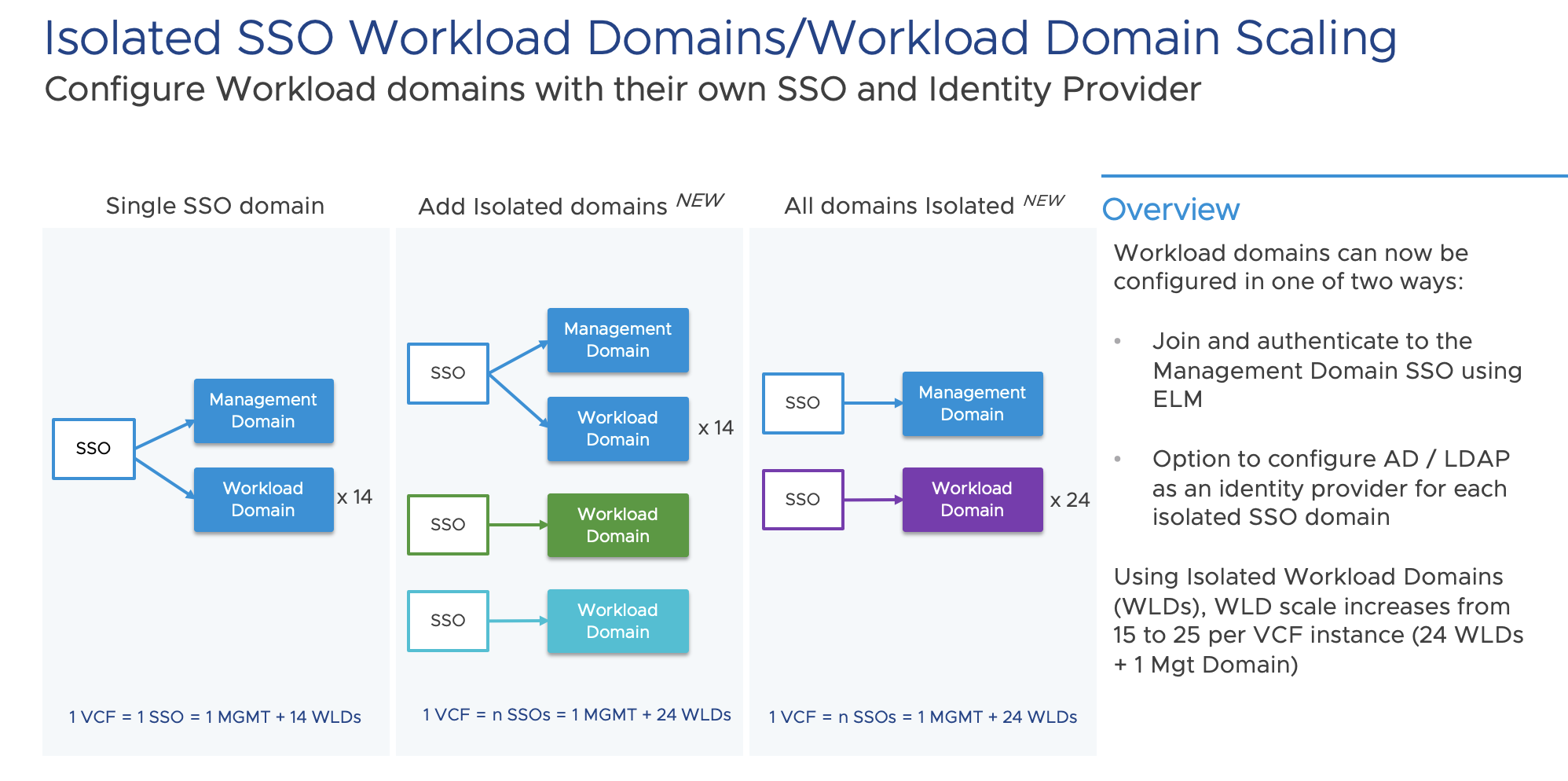
Workload Domain Scaling also increases when using isolated workload domains from 15 to 25 workload domains within a single VMware Cloud Foundation instance. Note that workload domains configured to use the shared management domain SSO are still limited to a maximum of 15 domains. Additional scaling is made possible through the parallelization of tasks in order to reduce the time to add Workload Domains within a VMware Cloud Foundation instance.
VMware Cloud Foundation Platform and Scaling Enhancements
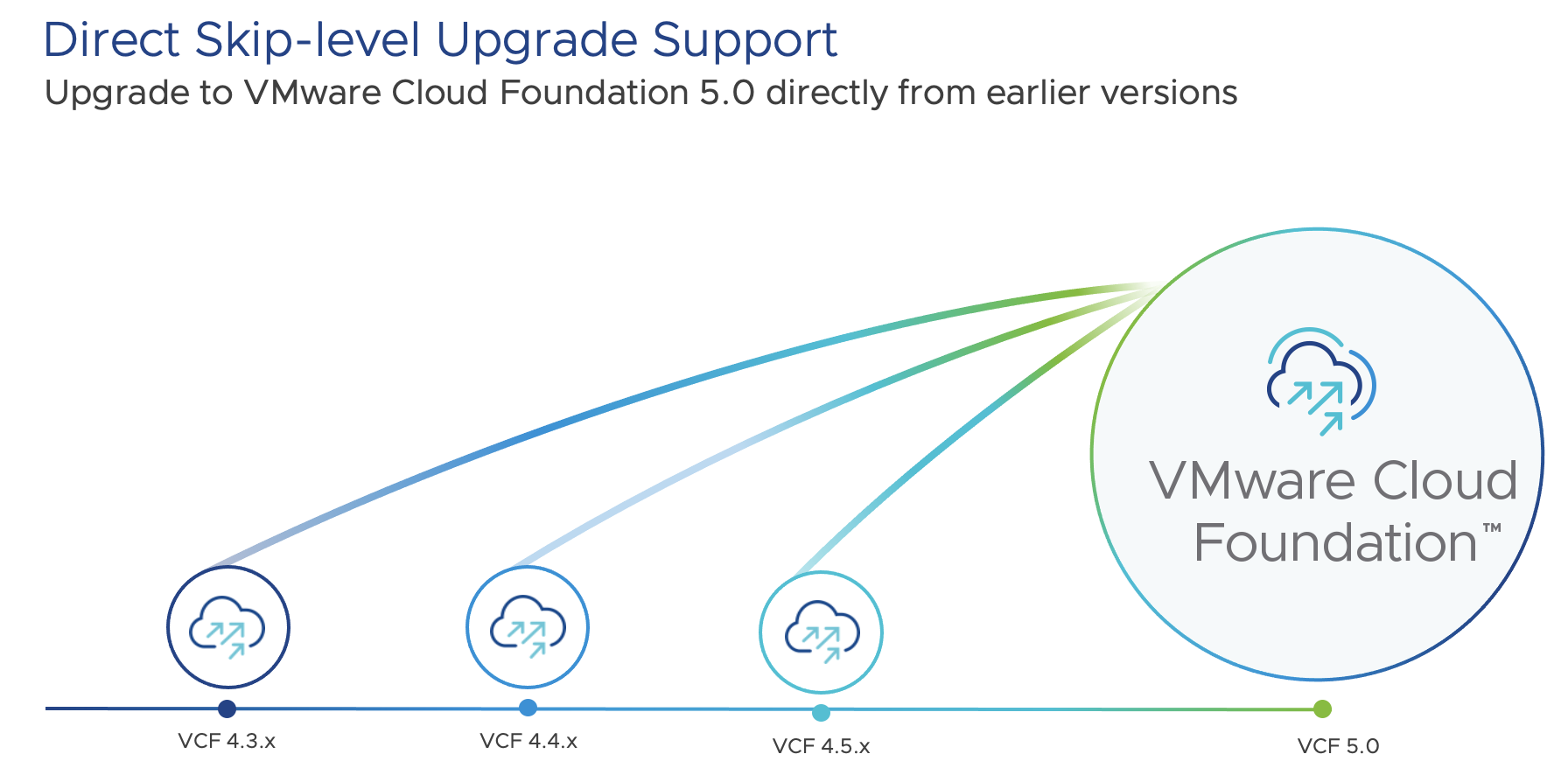
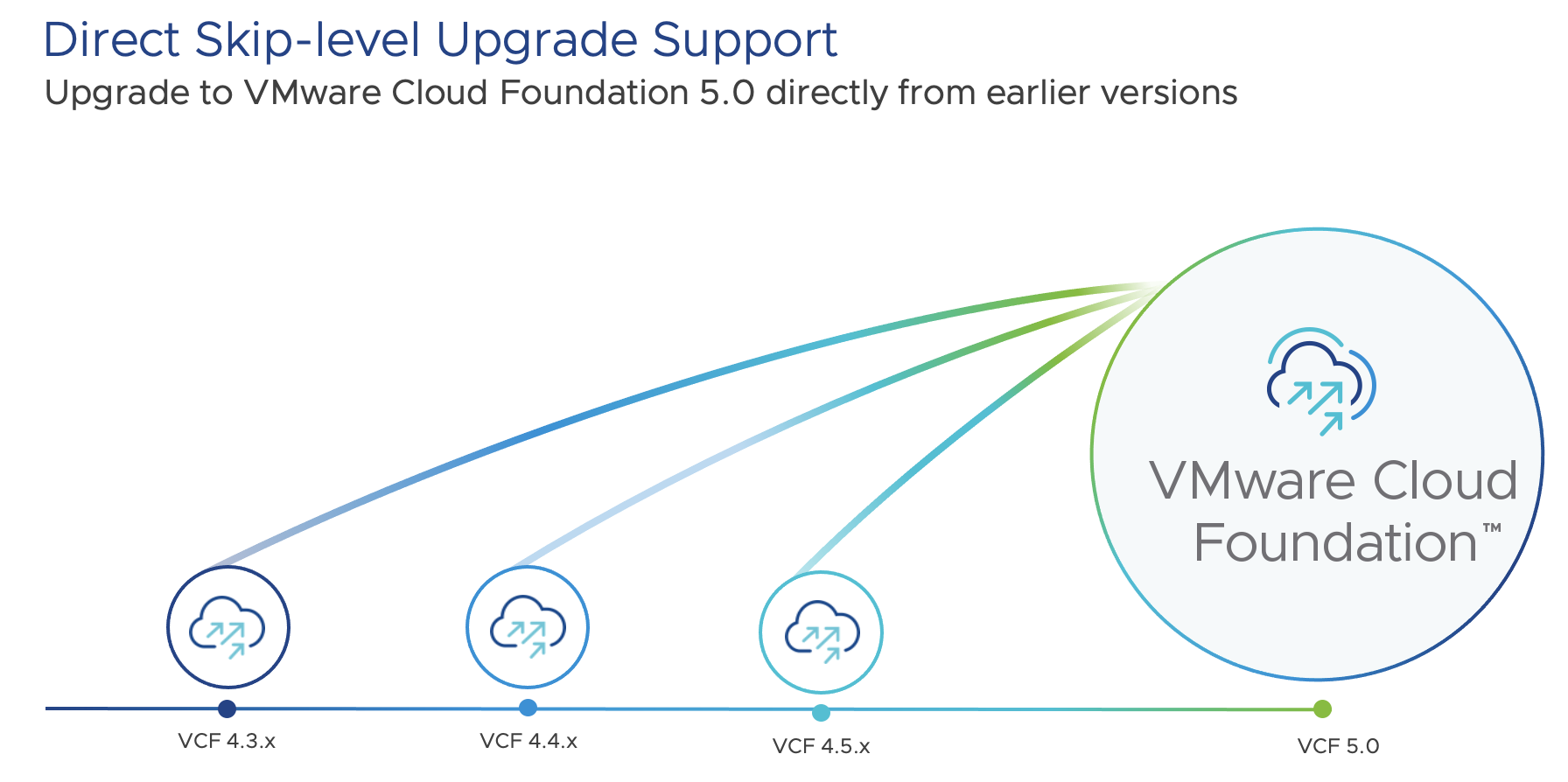
When one considers all of the new capabilities delivered within VMware Cloud Foundation 5.0, the platform and scale enhancements are probably the most highly anticipated customer feature requests, especially as they continue to scale their production of VMware Cloud Foundation environments. It is also important to emphasize that upgrades to VMware Cloud Foundation 5.0 are direct, customer led skip-level upgrades from VMware Cloud Foundation versions 4.3, 4.4 and 4.5.
More resources
https://blogs.vmware.com/cloud-foundation/2023/06/01/announcing-vmware-cloud-foundation-5-0/
https://blogs.vmware.com/cloud-foundation/?p=12521

