By Lerpong Intaraworrapath | 3rd June 2025
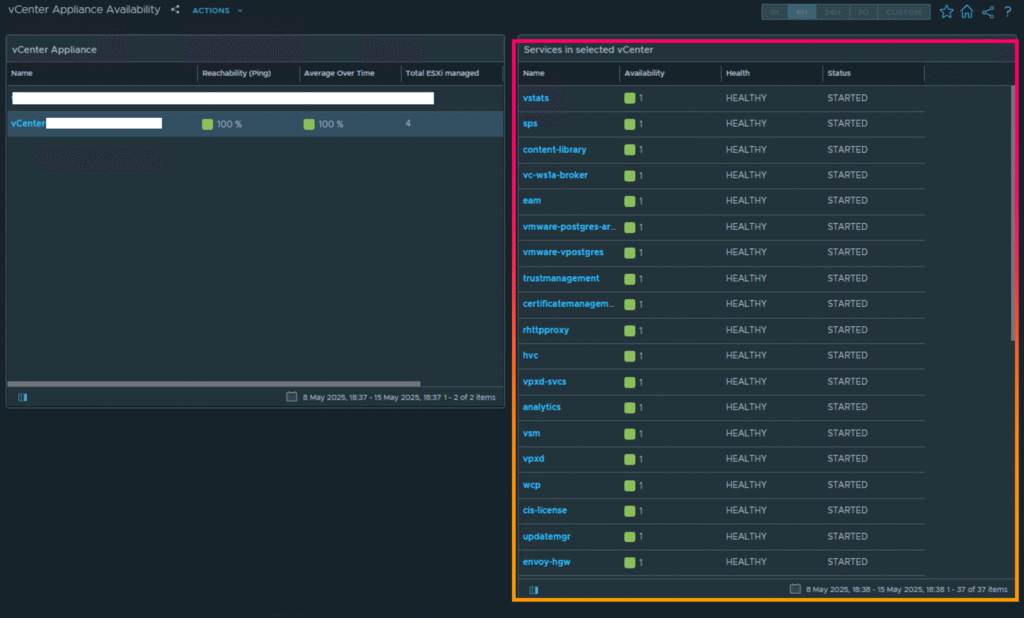
In Aria Operation 8.18, you may monitor vCenter Server services by going to the vCenter Appliance Availability dashboard.
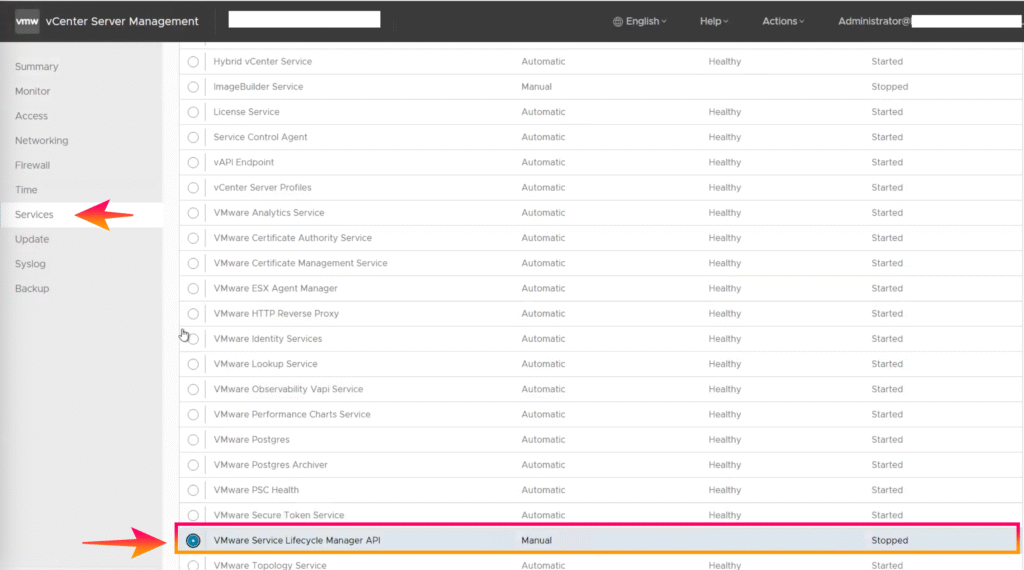
If you do not see vCenter and all its services, please check the VMware Service Lifecycle Manager API in the vCenter Appliance and start these services. (In vCenter Server Management versions 8.0.3 and above, the start type must be set to automated).
Step-by-Step
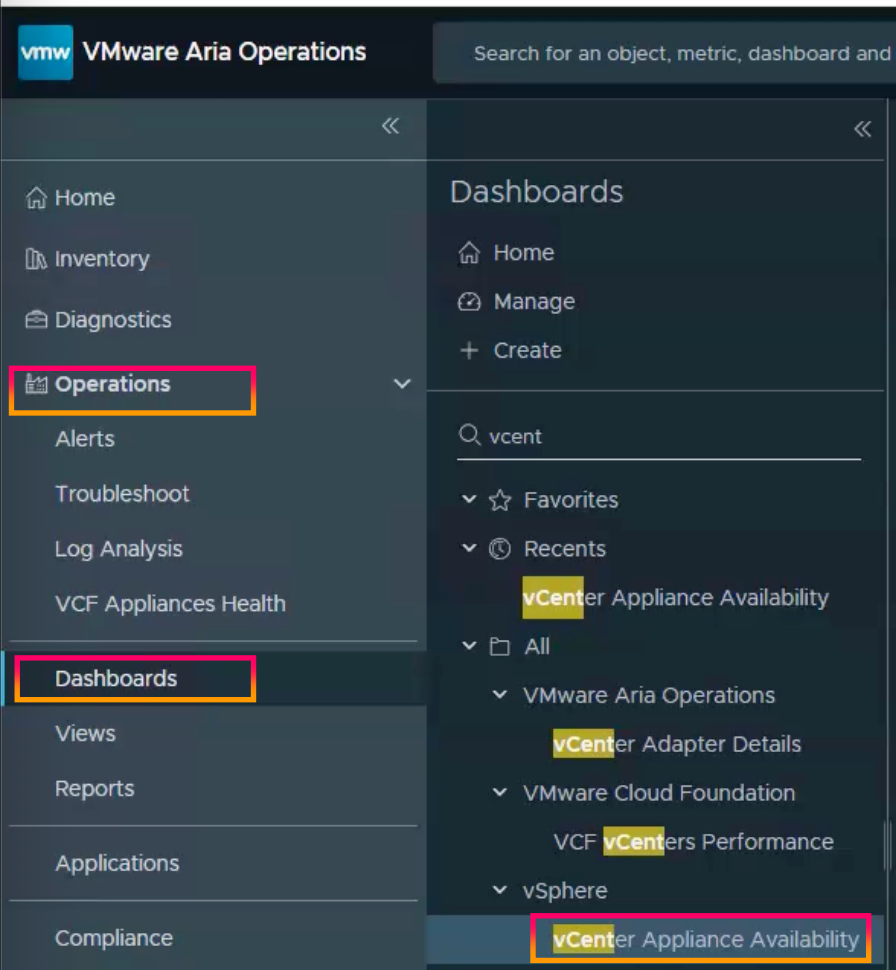
1.Log in to Aria Operations and go to “Operations” then “Dashboards” to find the “vCenter Appliance Availability” Dashboard.
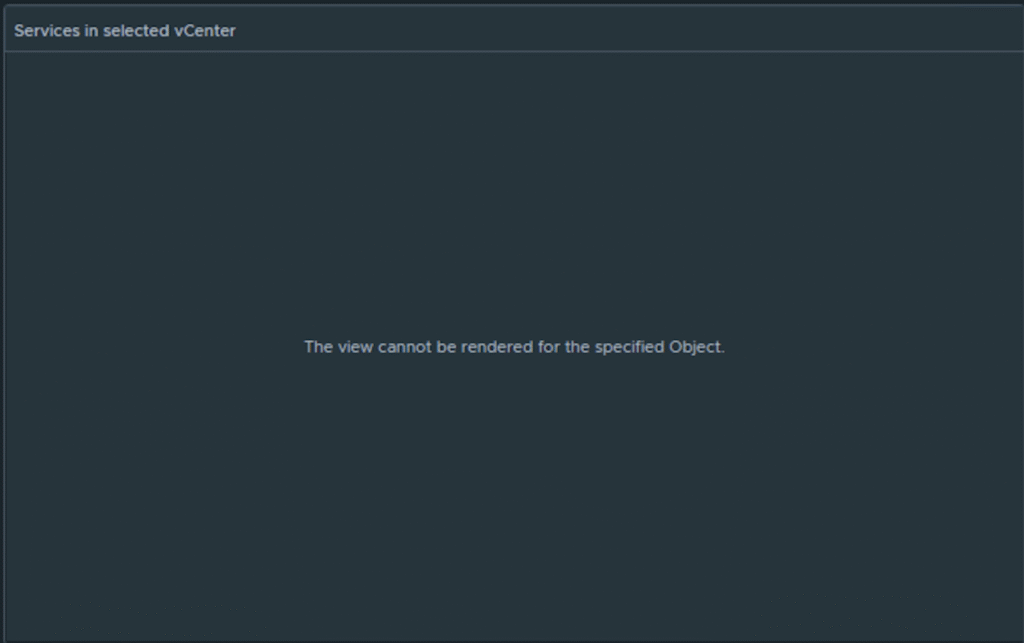
2.when you click on the vCenter Server. The entire vCenter Server is not visible, and you receive the message “The view cannot be rendered for the specified Object“.
3.Login to the vCenter server Appliance
4.In a Web browser, go to the vCenter Server Appliance Management Interface, https://appliance-IP-address-or-FQDN:5480.
5.You have to start the “VMware Service Lifecycle Manager API” from the vCenter Appliance. (Automated start needs to be performed in vCenter Server Management versions 8.0.3 and above).
6.Navigate to “Services” and select “VMware Service Lifecycle Manager API“.
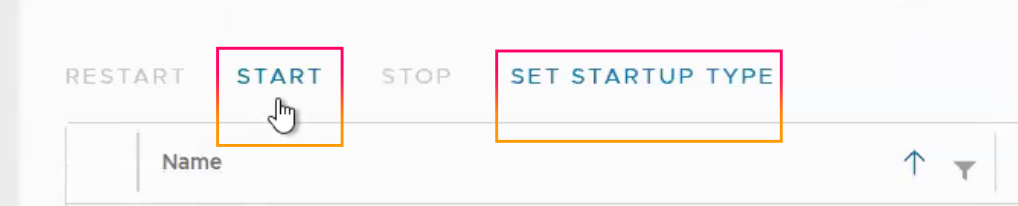
7.Click “START” and select “SET STARTUP TYPE“.
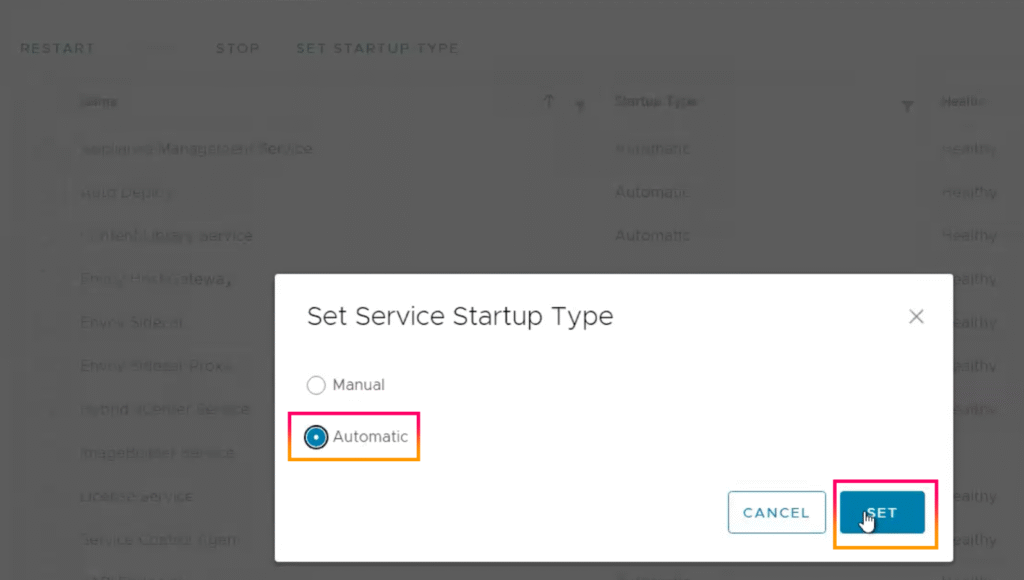
8.Set Service Startup Type to “Automatic” and click “SET“.
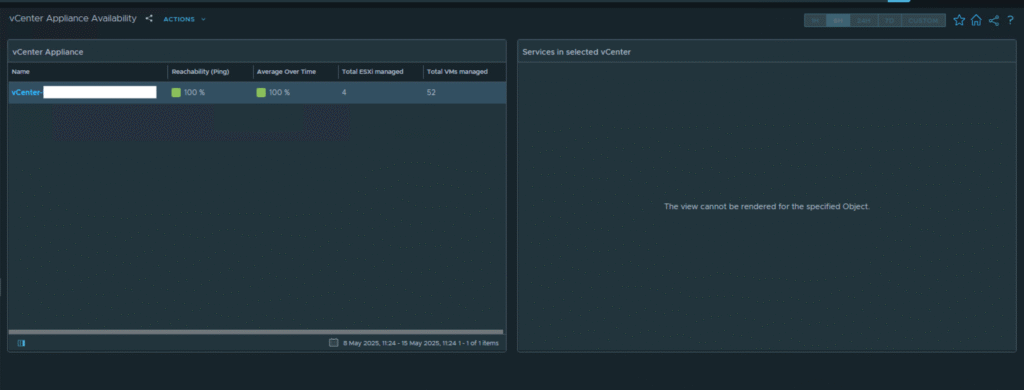
9.Wait 5 to 10 minutes before logging back into Aria Operations and selecting the “vCenter Appliance Availability” dashboard. Select “vCenter Server“, and the vCenter Server services will appear.